Dropbox just announced a partnership with Facebook that allows you to share your Dropbox files with fellow Facebook Group members. If you read through the comments on Dropbox's post, the reactions are mixed, with some stating they will stop using Dropbox altogether. Many of the negative reactions look to be due to issues with Facebook's track record and disregard towards privacy.
I should qualify this post by pointing out that this feature isn't active in my account yet so I haven't been able to test it. i.e. I could be wrong. Here are my initial thoughts based on what I've read.
Update (22 October 2012): I've tested it and my conclusions are correct.
At least we have some level of access control right? That's what it seems. But alas, not really.
You can only change this setting after the group has been created (if you actually know about it and can be bothered to go looking).
This seems to be done intentionally by Facebook to "encourage sharing and openness", as they sometimes like to put it. If you understand user behaviour, you'll know that because of this, for almost every single group defined in Facebook, any member is going to be able to add others to the group.
How is this a problem? The fact that any member within the group can add others means the group is effectively a public forum with the minor hurdle being that you have to convince a member to invite you. It's about as good as saying you're throwing a private party and assuming no one is going to give your address to one of their friends that you didn't explicitly invite. In other words, your file can potentially be seen by other people you never intended to give access to. In posting your file to the group, you are effectively delegating control over the read-only rights on your file to every member of the group.
None of this actually matters of course, because of the next issue.
Like I said, I haven't been able to test this, but...
Update (22 October 2012): I've tested it and my conclusions are correct.
Dropbox's own help page for this topic gives us this little bit of genius under the heading "Your links are secure" (emphasis added by me):
But the real kicker is that none of this matters because anyone that has access to the link can use it to gain direct access to the file and forward that link on to the public. The only saving grace is that it doesn't look like anyone has write access on the file other than the owner.But I haven't been able to test this just yet so who knows. Update (22 October 2012): I've tested it and my conclusions are correct.
In short, if you share your file with a Facebook Group, you've just made it public.
Update (22 October 2012): I've tested it and my conclusions are correct.
Access control
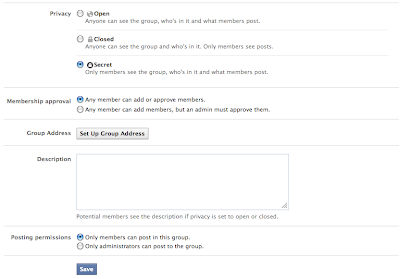
First of all, the access controls are not sufficiently granular. Access is tied to a group which means if you post a file, anyone in that group can read it. There doesn't seem to be an option for more granular control. Sure, you could create more groups and add the people you want to them. But those of you in the Identity & Access Management world know what happens when you constantly add roles/groups within an environment for additional segregation. Pretty soon, you'll have more groups than friends.At least we have some level of access control right? That's what it seems. But alas, not really.
Every group member is effectively an administrator
When you create a group in Facebook, the default setting is to allow any member to add other people to the group. When you create a group, it's not even an option to make the informed decision.You can only change this setting after the group has been created (if you actually know about it and can be bothered to go looking).
This seems to be done intentionally by Facebook to "encourage sharing and openness", as they sometimes like to put it. If you understand user behaviour, you'll know that because of this, for almost every single group defined in Facebook, any member is going to be able to add others to the group.
How is this a problem? The fact that any member within the group can add others means the group is effectively a public forum with the minor hurdle being that you have to convince a member to invite you. It's about as good as saying you're throwing a private party and assuming no one is going to give your address to one of their friends that you didn't explicitly invite. In other words, your file can potentially be seen by other people you never intended to give access to. In posting your file to the group, you are effectively delegating control over the read-only rights on your file to every member of the group.
None of this actually matters of course, because of the next issue.
Security by obscurity
Update (22 October 2012): I've tested it and my conclusions are correct.
Dropbox's own help page for this topic gives us this little bit of genius under the heading "Your links are secure" (emphasis added by me):
"When you share a link, Dropbox creates a unique token used only in that link. It is almost impossible to guess the token, but even if someone was able to, they'd have to know the name of the folder and files the link points to. That said, anyone who can see the link can copy it and post it elsewhere, such as another website."So let me get this straight. They've used "almost" to qualify themselves out of being at fault if someone "leaks" your data and basically said your link isn't really secure under the heading that states "your links are secure".
Conclusion
I've just taken you through my discovery process upon digging a little deeper. At first, I thought that there was at least a level of access control, albeit very coarse-grained. But by default, every group member is effectively an administrator, hence anyone can grant read permission on files within the group without approval from the owner. So there's actually no access control, merely the appearance that there is.But the real kicker is that none of this matters because anyone that has access to the link can use it to gain direct access to the file and forward that link on to the public. The only saving grace is that it doesn't look like anyone has write access on the file other than the owner.
In short, if you share your file with a Facebook Group, you've just made it public.