This year, the public presentation I gave more than any other was titled: "Identity in an agile world". I put this together specifically for events in Sydney, Melbourne, Singapore, Kuala Lumpur, Wellington, Auckland, Bangalore, Mumbai, Taiwan and Hong Kong.
The most common question after each event was whether we could provide a recording of the session. The best I could do at the time was to send the slide deck to attendees. The next best thing is what I'm about to do: a blog post in the style of a presentation.
As this is a presentation masquerading as a blog post, it will be different to my usual posts. There are a bunch of images littered throughout, which are all slides from my presentation deck (I've actually omitted a few, but this shouldn't affect the overall content). As a result, you'll see some text as images because they were slides. I've kept it this way instead of typing everything out to give you a better feel for the actual presentation.
Note: This was not intended as a technical presentation. There's some IAM101 in here too, so feel free to skim when required.
As enterprise trends go in 2012, Cloud and mobility have dominated the headlines. Almost every survey, study, whitepaper and article you read will talk about the pressure organisations are feeling in trying to deal with the seemingly unmanageable. Of course, the increased sophistication and frequency of attacks adds to the pressure. Top it off with further reduced budgets (which seems to be an issue regardless of the year) and IT departments having to do more with less and you very quickly have everyone in the room collectively shrugging.
If you ask anyone who has had to deal with these pressures, they will tell you that scalability is paramount. If you cannot scale, forget about it. To scale, you need to be agile, not just from a security standpoint, but from an organisational standpoint. IT departments need to be able to integrate and secure new systems quickly and also react to issues, risks and requirements much faster than they are used to. If they don’t, business users will go around them and do things themselves.
The biggest concern facing organisations however, is security. How do you secure something which you do not have full control over? The enterprise perimeter’s been disappearing for some time now, but I think we can all agree that the traditional enterprise perimeter is well and truly gone when Cloud and mobility come into play.
There’s a popular school of thought that says identity is the new perimeter.
That’s one way to look at it, but it's the wrong perspective even though I don't disagree with it from a fundamental standpoint. It's wrong because it means we’re still thinking about perimeters. We must think of identity as a foundation on top of which enterprise security is built. This way, we no longer need to worry about whether there is a perimeter that you can control.
Identity management as a discipline can be very complex. Like most things, I find it easier to simplify. All we’re trying to do is to provide auditable access to protected resources that we can track, regardless of where we’re coming from and what we’re using to access the resources. That’s it.
Before I move on, let’s run through a quick history lesson of the Identity and Access Management (IAM) industry. This is an extremely simplified version so please forgive any omissions.
The last major paradigm shift in computing before this one we are currently experiencing came about as a result of the move towards distributed systems from primarily mainframe environments. With that came a problem with identities being stored in multiple places and having no way to manage them in a practical way.
So we decided to attempt using centralised directories for everything. We said: “hey, let’s just have a single identity store and make everything point there”.
It made sense at the time, but this was not always practical or even feasible. What this did do was reduce the number of identity stores. But we still had the siloed identity issue. To address this, we then decided to use synchronisation tools.
This worked just fine until those troublesome business folks got involved and wanted to wrap process around it. That’s essentially how we got to user provisioning solutions.
Once we had a process-oriented way to move our identities around, we then had to figure out how to control access to resources while hiding the nastiness from our users but maintaining an acceptable level of security. This gave us username/password authentication augmented with second and third factors, single sign-on and access control solutions to all these systems that we needed to use for our jobs.
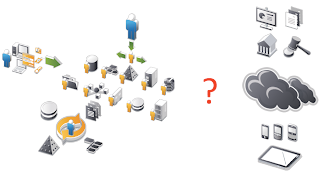
Here’s a consolidated view of what I’ve just explained; the technical IAM big picture.
This is a very enterprise-centric view of the world. So what happens when you throw in a few new challenges?
Other than Cloud and mobility, we have to deal with audit, governance and compliance requirements and locking down those pesky privileged users that can do anything they want. Ideally, we’d like to re-use what we’ve already implemented. But as I alluded to earlier, we can only use what we already have if the current infrastructure will scale. In addition, we need to think about this a little differently; we need a scalable, agile identity.
We need to wrap our minds around this new-fangled way to think about IAM, but where do we find a scalable identity management system? What is a scalable, agile identity?
Like many other things, we can actually borrow from the real world because that’s where things generally work. We’ve actually had one for many years.
A passport is the primary form of identification for most of us; it is typically the strongest physical identification method we have. It asserts that I’m a citizen of this country.
Whenever I get on a plane...
To get to a different country...
The officers at the airport let me in because they recognise the passport as being genuine (by performing relevant checks)...
And that it has been issued by a Government they trust, in my case Australia.
This is another form of identification.
For most of us, this is our secondary form of identification. It also happens to be the one we use more often. This one says something else about me; that I live in this city.
Both forms of identification state when I was born, but...
Why? Let’s look at an example. This is the Bellagio in Las Vegas.
When I go to a casino in the US, they care that I’m over 21. That’s the condition of entry. But they won’t accept this as proof.
They need this.
Here’s another example. Whenever I want to go to one of these places...
To have one of these...
They don’t care how old I am. In the US, they just care that I’m over 21.
In Australia, they care that I’m over 18.
It's that...
Identity in the real world is about reputation, context and trust.
Reputation can be made up of multiple things which an entity might store about me, but it also has a lot to do with where I’m from and the demographic I fit into. We've all been unfairly stereotyped before. Unfortunately, this is part of the reputation angle. Decisions can be made based on things that are implied about us no matter how unfair or untrue. Context is all about what I’m trying to do or get access to. Trust is about whether the form of identification I’m using (i.e. my credential) is genuine and issued by a reputable, trusted party in the context of what I’m doing and where I’m doing it.
Once I get past the controls however, I can misuse my legitimate access or in some cases, much worse. Alternatively, someone or something may have stolen my credentials to be able to pose as me. Access control systems have no real way of knowing. That's how many real life crimes and frauds are committed. "Who I am" doesn’t matter. It's not even about the "what I am" anymore. Both of these aspects are irrelevant or useless given the circumstances. With the right access...
To account for this, we need a new dimension on top of identity. We need to track behaviour.
We hear about breaches almost weekly now. There are many others that never get reported. The fact is that they happen all the time.
The key to minimising the fallout if something does happen is the ability to react quickly. You need identity and behavioural analysis to help determine the appropriate steps to take.
If not, you’re sitting there with the knowledge that something bad is happening but powerless to stop it.
In the real world, privacy laws prevent measures from going beyond what we deem to be acceptable, but we’re more or less a surveillance society nowadays. Add our online personas and social networking profiles into the mix and never has it been easier to intrude on someone's privacy.
Take a look at this for a minute (click on the image for the larger version)...
Something like what you see here isn’t completely outside of the realm of possibility. We just need a few technologies to get better (facial recognition being the obvious candidate for improvement) and we’re pretty much here (especially with Google Glasses). Cutting-edge technology aside, let's think about how is this even remotely possible. Give up? It's because...
With an enterprise identity foundation that is scalable, you can absolutely do this from an organisational risk management and threat mitigation standpoint. But how does an enterprise do it? As I've said before, Standards and APIs are key. This needs to work hand-in-hand with portable, embeddable, sharable enterprise credentials (identities).
In the real world, we can't exactly do a lot with regards to the items in red (at least not legally). But all the data within enterprise-owned systems is accessible to allow for this. More on that after this next part.
I've tried to keep technology to a minimum, but I felt the need to at least summarise the most commonly used standards today and their purposes.
I won't explain what each of these are. You're all capable of looking them up. Some of these will evolve to take on other use cases. Some will cease to be relevant. If I had to bet, my money would be on the standards being used in the consumer space making their way into the enterprise, not the other way around.
Now, back to the items in red from the previous slide. Let's talk about the behavioural analysis side of things. I’m going to borrow again from the real world; well, almost real.
This is a screen shot from the World of Warcraft. Apart from the graphics and virtual world, massively multiplayer online role-playing games (MMORPGs) are built on the foundation of identities. Without identities, we don’t have characters. More accurately, we don't have avatars in the game. When we walk through one of these virtual gaming worlds, we have displays that tell us who an avatar is and their relevant attributes. We make decisions very quickly based on the contextual information available whether the avatar is friend or foe; we decide whether to have them join our guild or zap them with weapons we have at our disposal as per this screen shot. Is this so different to what we should be doing when analysing the things going on in our enterprise environments?
If you don't remember a thing I've said (written), please remember this...
The fact that I've managed to spell out "SAVE" is completely coincidental, but hopefully it helps us SAVE it to memory.
The most common question after each event was whether we could provide a recording of the session. The best I could do at the time was to send the slide deck to attendees. The next best thing is what I'm about to do: a blog post in the style of a presentation.
As this is a presentation masquerading as a blog post, it will be different to my usual posts. There are a bunch of images littered throughout, which are all slides from my presentation deck (I've actually omitted a few, but this shouldn't affect the overall content). As a result, you'll see some text as images because they were slides. I've kept it this way instead of typing everything out to give you a better feel for the actual presentation.
Note: This was not intended as a technical presentation. There's some IAM101 in here too, so feel free to skim when required.
As enterprise trends go in 2012, Cloud and mobility have dominated the headlines. Almost every survey, study, whitepaper and article you read will talk about the pressure organisations are feeling in trying to deal with the seemingly unmanageable. Of course, the increased sophistication and frequency of attacks adds to the pressure. Top it off with further reduced budgets (which seems to be an issue regardless of the year) and IT departments having to do more with less and you very quickly have everyone in the room collectively shrugging.
If you ask anyone who has had to deal with these pressures, they will tell you that scalability is paramount. If you cannot scale, forget about it. To scale, you need to be agile, not just from a security standpoint, but from an organisational standpoint. IT departments need to be able to integrate and secure new systems quickly and also react to issues, risks and requirements much faster than they are used to. If they don’t, business users will go around them and do things themselves.
The biggest concern facing organisations however, is security. How do you secure something which you do not have full control over? The enterprise perimeter’s been disappearing for some time now, but I think we can all agree that the traditional enterprise perimeter is well and truly gone when Cloud and mobility come into play.
There’s a popular school of thought that says identity is the new perimeter.
That’s one way to look at it, but it's the wrong perspective even though I don't disagree with it from a fundamental standpoint. It's wrong because it means we’re still thinking about perimeters. We must think of identity as a foundation on top of which enterprise security is built. This way, we no longer need to worry about whether there is a perimeter that you can control.
Identity management as a discipline can be very complex. Like most things, I find it easier to simplify. All we’re trying to do is to provide auditable access to protected resources that we can track, regardless of where we’re coming from and what we’re using to access the resources. That’s it.
Before I move on, let’s run through a quick history lesson of the Identity and Access Management (IAM) industry. This is an extremely simplified version so please forgive any omissions.
The last major paradigm shift in computing before this one we are currently experiencing came about as a result of the move towards distributed systems from primarily mainframe environments. With that came a problem with identities being stored in multiple places and having no way to manage them in a practical way.
So we decided to attempt using centralised directories for everything. We said: “hey, let’s just have a single identity store and make everything point there”.
It made sense at the time, but this was not always practical or even feasible. What this did do was reduce the number of identity stores. But we still had the siloed identity issue. To address this, we then decided to use synchronisation tools.
This worked just fine until those troublesome business folks got involved and wanted to wrap process around it. That’s essentially how we got to user provisioning solutions.
Once we had a process-oriented way to move our identities around, we then had to figure out how to control access to resources while hiding the nastiness from our users but maintaining an acceptable level of security. This gave us username/password authentication augmented with second and third factors, single sign-on and access control solutions to all these systems that we needed to use for our jobs.
Here’s a consolidated view of what I’ve just explained; the technical IAM big picture.
This is a very enterprise-centric view of the world. So what happens when you throw in a few new challenges?
Other than Cloud and mobility, we have to deal with audit, governance and compliance requirements and locking down those pesky privileged users that can do anything they want. Ideally, we’d like to re-use what we’ve already implemented. But as I alluded to earlier, we can only use what we already have if the current infrastructure will scale. In addition, we need to think about this a little differently; we need a scalable, agile identity.
We need to wrap our minds around this new-fangled way to think about IAM, but where do we find a scalable identity management system? What is a scalable, agile identity?
Like many other things, we can actually borrow from the real world because that’s where things generally work. We’ve actually had one for many years.
A passport is the primary form of identification for most of us; it is typically the strongest physical identification method we have. It asserts that I’m a citizen of this country.
Whenever I get on a plane...
To get to a different country...
The officers at the airport let me in because they recognise the passport as being genuine (by performing relevant checks)...
And that it has been issued by a Government they trust, in my case Australia.
This is another form of identification.
For most of us, this is our secondary form of identification. It also happens to be the one we use more often. This one says something else about me; that I live in this city.
Both forms of identification state when I was born, but...
They only care that I’m...
and
and
and
Why? Let’s look at an example. This is the Bellagio in Las Vegas.
When I go to a casino in the US, they care that I’m over 21. That’s the condition of entry. But they won’t accept this as proof.
They need this.
Here’s another example. Whenever I want to go to one of these places...
To have one of these...
They don’t care how old I am. In the US, they just care that I’m over 21.
In Australia, they care that I’m over 18.
So...
It's that...
...
...
Identity in the real world is about reputation, context and trust.
Reputation can be made up of multiple things which an entity might store about me, but it also has a lot to do with where I’m from and the demographic I fit into. We've all been unfairly stereotyped before. Unfortunately, this is part of the reputation angle. Decisions can be made based on things that are implied about us no matter how unfair or untrue. Context is all about what I’m trying to do or get access to. Trust is about whether the form of identification I’m using (i.e. my credential) is genuine and issued by a reputable, trusted party in the context of what I’m doing and where I’m doing it.
Once I get past the controls however, I can misuse my legitimate access or in some cases, much worse. Alternatively, someone or something may have stolen my credentials to be able to pose as me. Access control systems have no real way of knowing. That's how many real life crimes and frauds are committed. "Who I am" doesn’t matter. It's not even about the "what I am" anymore. Both of these aspects are irrelevant or useless given the circumstances. With the right access...
To account for this, we need a new dimension on top of identity. We need to track behaviour.
We hear about breaches almost weekly now. There are many others that never get reported. The fact is that they happen all the time.
The key to minimising the fallout if something does happen is the ability to react quickly. You need identity and behavioural analysis to help determine the appropriate steps to take.
If not, you’re sitting there with the knowledge that something bad is happening but powerless to stop it.
In the real world, privacy laws prevent measures from going beyond what we deem to be acceptable, but we’re more or less a surveillance society nowadays. Add our online personas and social networking profiles into the mix and never has it been easier to intrude on someone's privacy.
Take a look at this for a minute (click on the image for the larger version)...
Something like what you see here isn’t completely outside of the realm of possibility. We just need a few technologies to get better (facial recognition being the obvious candidate for improvement) and we’re pretty much here (especially with Google Glasses). Cutting-edge technology aside, let's think about how is this even remotely possible. Give up? It's because...
With an enterprise identity foundation that is scalable, you can absolutely do this from an organisational risk management and threat mitigation standpoint. But how does an enterprise do it? As I've said before, Standards and APIs are key. This needs to work hand-in-hand with portable, embeddable, sharable enterprise credentials (identities).
In the real world, we can't exactly do a lot with regards to the items in red (at least not legally). But all the data within enterprise-owned systems is accessible to allow for this. More on that after this next part.
I've tried to keep technology to a minimum, but I felt the need to at least summarise the most commonly used standards today and their purposes.
I won't explain what each of these are. You're all capable of looking them up. Some of these will evolve to take on other use cases. Some will cease to be relevant. If I had to bet, my money would be on the standards being used in the consumer space making their way into the enterprise, not the other way around.
Now, back to the items in red from the previous slide. Let's talk about the behavioural analysis side of things. I’m going to borrow again from the real world; well, almost real.
This is a screen shot from the World of Warcraft. Apart from the graphics and virtual world, massively multiplayer online role-playing games (MMORPGs) are built on the foundation of identities. Without identities, we don’t have characters. More accurately, we don't have avatars in the game. When we walk through one of these virtual gaming worlds, we have displays that tell us who an avatar is and their relevant attributes. We make decisions very quickly based on the contextual information available whether the avatar is friend or foe; we decide whether to have them join our guild or zap them with weapons we have at our disposal as per this screen shot. Is this so different to what we should be doing when analysing the things going on in our enterprise environments?
If you don't remember a thing I've said (written), please remember this...
The fact that I've managed to spell out "SAVE" is completely coincidental, but hopefully it helps us SAVE it to memory.













































No comments:
Post a Comment